


Check here our top 5 Extension Mobility security threats. Extension Mobility is without doubt one of the most useful functions of Cisco’s VoIP and Unified Communications solutions. Users are no longer bounded to a fixed access point or device, but can register themselves to any IP telephone in the office. They simply login on the device and from that moment they can be reached via their own extension number, while their profile and features are activated for that telephone as well. However, ‘simply login’ is perhaps an understatement…
Each time a user wants to register himself on a device, he has to login with a username and a password. The username is in many implementations the user’s email address, which means that users have to type in long email addresses and complex passwords using the very basic keypad of their Cisco desktop telephone. It also means that they have to remember one additional password.
The impact of this is clearly illustrated by this forum discussion we found on the internet. A service manager discusses the problem of employees who are using the extension mobility feature but forget their pin codes. The reply from a colleague suggests to keep their phones logged in as long as they use the same desk for a longer period (which is often the case, even in flex offices). It is an advice we often hear. It works, but is of course highly insecure. 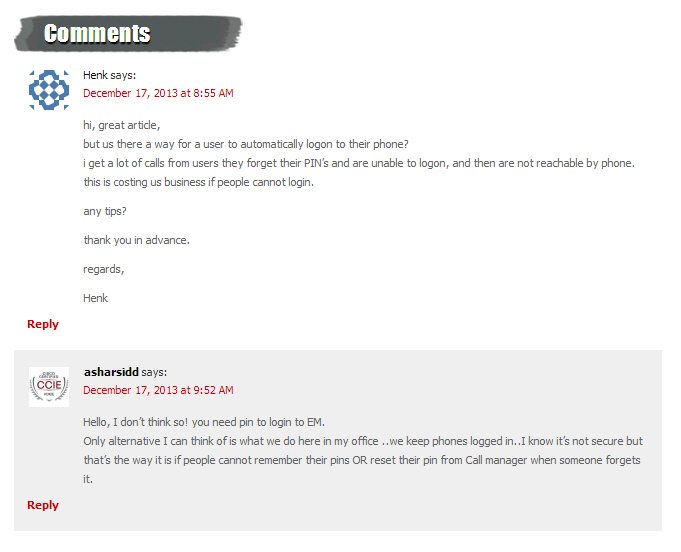 Forum discussion between IP Telephony service managers, suggesting to use Extension Mobility (EM) in a non-secured way. A disputable advice in my opinion.
Forum discussion between IP Telephony service managers, suggesting to use Extension Mobility (EM) in a non-secured way. A disputable advice in my opinion.
So, you keep your IP phones logged in all the time? What’s the problem? Indeed, very often people don’t see any risk in non-secured phone extensions. It is just a phone, not even a smartphone and it is definitely not a laptop or tablet with full access to the company’s computer network and data. So, the impact of unauthorized access to a desktop telephone is rather small, isn’t it?
Unfortunately, this is only partly true. Current desktop IP telephone devices are indeed not smartphones, but they are developing extremely fast towards very smart and intelligent devices with access to your data network. And indeed they are not having the same functionality as your laptop or tablet, but nevertheless you would be shocked if you realized how at least some of your sensitive company data could be accessed via a non-secured IP Telephone. In this blog, I give you a few – only the top 5 – security risks which you and your organization face when your employees keep their desktop IP phones logged in day and night.
Phone conversations which your employees have with clients, patients, business partners or colleagues may be very confidential. Normally the contents of a call can only be eavesdropped in case a phone line is being tapped. However, people not only talk to each other, they also use voicemail to exchange information, sometimes even very private and confidential information. Normally, only the registered user can listen to his or her voicemail, but if an IP phone is logged in, anyone with access to that phone can access the user’s voicemail. What if an unauthorized user can listen to the voicemails of a medical expert? What if someone can access the voicemails of a public servant who is coordinating a complex and sensitive dossier? Just think about the News of the World scandal and you know what the impact could be.
Contact information is very useful information. Who is who in a company is basic information, but the direct telephone numbers of key staff and managers are often hard to find. Think for example about the restrictions in an application like LinkedIn. You can find all information about people on such business networks, but the direct contact information is hidden from you. How much easier would it be if you could have direct numbers of key staff instead of being connected to a secretary who often acts as a firewall for cold callers?
This is even more the case for the personal directory of individual business users. This personal directory is part of their VoIP profile and stored in the company’s telephony database. If someone has access to an open desktop telephone, he or she has also access to the personal directory of the user of that VoIP account. This could mean for example that you can have direct access to the full contact list of an account manager, the confidential client list of a medical expert or the list of close advisers to a politician. In brief, you simply have access to the entire network of a person, with all their direct numbers.
As we all know, the caller ID matters. If a call is indicated as originating from an organization, company or person we know, we tend to trust the calling person. With Caller IDs which we don’t recognize or even anonymous callers we are typically far more cautious. Criminals therefore explore all possibilities for Caller ID spoofing. Caller ID spoofing techniques alter the caller ID into a number which will be trusted by a receiving party. They use this to identify themselves as a bank, the police or other authorities, your internet provider, a debt collector etc. etc… And although many people recognize fraud attempts by phone, if just a small percentage doesn’t recognize this, which is sufficient for the fraudsters.
Take for example the Evening Standard article ‘Nine arrested over ‘£60 million fraud’ targeting bank customers’ (2015). In this fraud scenario, criminals used technology to disguise the number they called from. Apparently calling from a legitimate bank, they contacted business customers in order to dupe them into revealing personal information. The criminals used the information to get access to the bank accounts. How does this work within a corporate network?
For example, how can someone abuse the telephone network to make social engineering calls to employees of a company? The first step is to present himself, via the Caller ID, as a direct colleague. Caller ID Spoofing solutions from an outside line often won’t work for this, since external calls typically differ from internal calls in terms of sound characteristics, ringing signals etc. However, an open VoIP extension, logged in and ready for use, is the perfect tool for making social engineering calls. Take for example an employee who receives an internal call from a colleague at e.g. the financial department. The caller knows his name and asks for specific information about a new project. Many people will give their internal colleague all the information he or she asks for, even if the information requested is confidential.
An Extension Mobility user can activate the call forwarding feature. This feature takes care of forwarding all calls to another destination number, for example a mobile number. Think of the impact when an unauthorized user activates this functionality and reroutes all incoming calls to another destination number or voicemail.
In the introduction of this article, I showed a discussion between two VoIP service managers. One advised the other to use the Extension Mobility login procedure only at first use and keep the phone logged in from that moment on in order to prevent the problem of employees who forget to log in or who forget their passwords. I also showed that this could be a bad advice. There are numerous scenarios’ in which abuse can be made of a VoIP telephone which is logged in and unobserved. From accessing voicemail to social engineering activities, they are all possible.
It is good to know that there is actually a perfect solution to use the Cisco Extension Mobility features in a very secure way, without the need to type in long strings of usernames and passwords every morning and without the need to remember additional passwords. Using our ALM Single Sign On (SSO) solution it is no longer necessary for Extension Mobility users to login to their telephone. In case they login to their work-space (laptop or PC), they automatically login to the Cisco IP Phone on their desk as well. ALM protects your Cisco Device against unauthorized use and is a must-have for companies using Cisco IP Telephony, Cisco Unified Communications (CUCM) and Cisco Call Manager technology (CCM). The software is easy to use and improves the internal security policies within your company, optionally on top of your current Active Directory integration. Deploying the ALM software give you all the benefits of the Extension Mobility features, without negative impact on your communications security levels.